My fellow colleague Vincent Riccio described here in his blog post the open-source SaltStack Modules that provide hooks into components such as VMware Cloud on AWS, NSX-T, and vSphere.
These modules are a fantastic way to implement prescriptive configuration management across various VMware infrastructure components using the same solution as you should use for software and configuration management of your operating systems and applications – vRealize Automation SaltStack Config.
In this blog post, I will show you how easy it is to install and use the Salt Extension Modules for VMware using the vSphere vCenter module as an example.
Pre-Requisites
I have modified the following Quickstart to fit into my SaltStack setup.
The components running in my lab for this quick demo are:
- vRealize Automation SaltStack Config instance
- SaltStack minion on a Linux VM
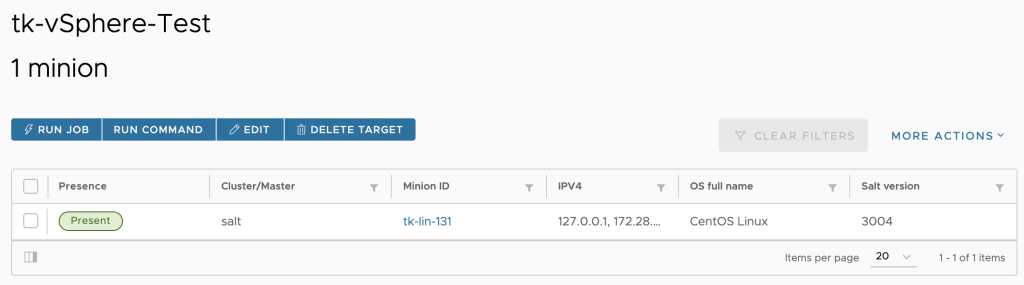
The next picture shows my Salt minion running in a CentOS 8 Linux. This minion will be the dedicated minion I will use to execute the VMware modules.
Configuration Steps
Step 1: We need to provide basic information to let SaltStack connect to the vCenter Server. Usually, we use Salt pillars to specify such configuration variables. In the next picture, you see the pillar I have created for my vCenter instance.
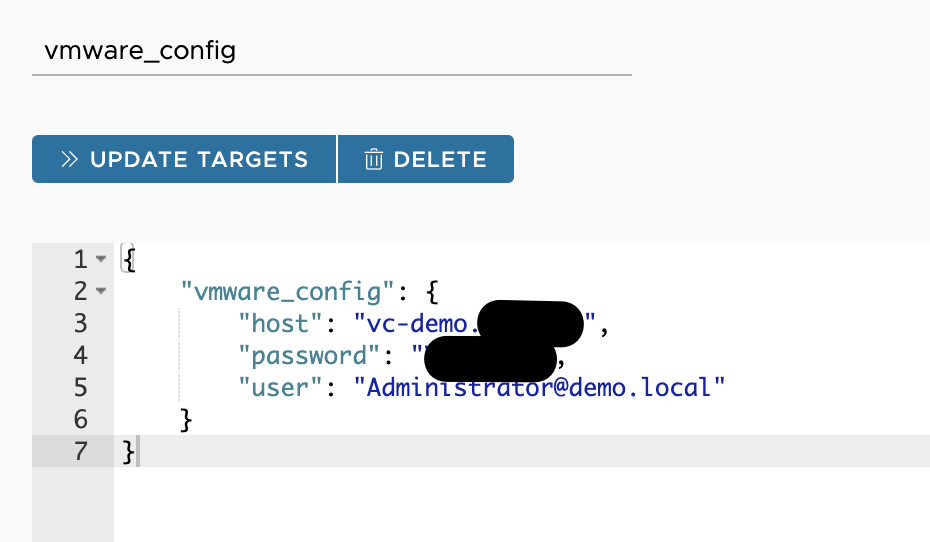
Please be aware that the user name is case sensitive.
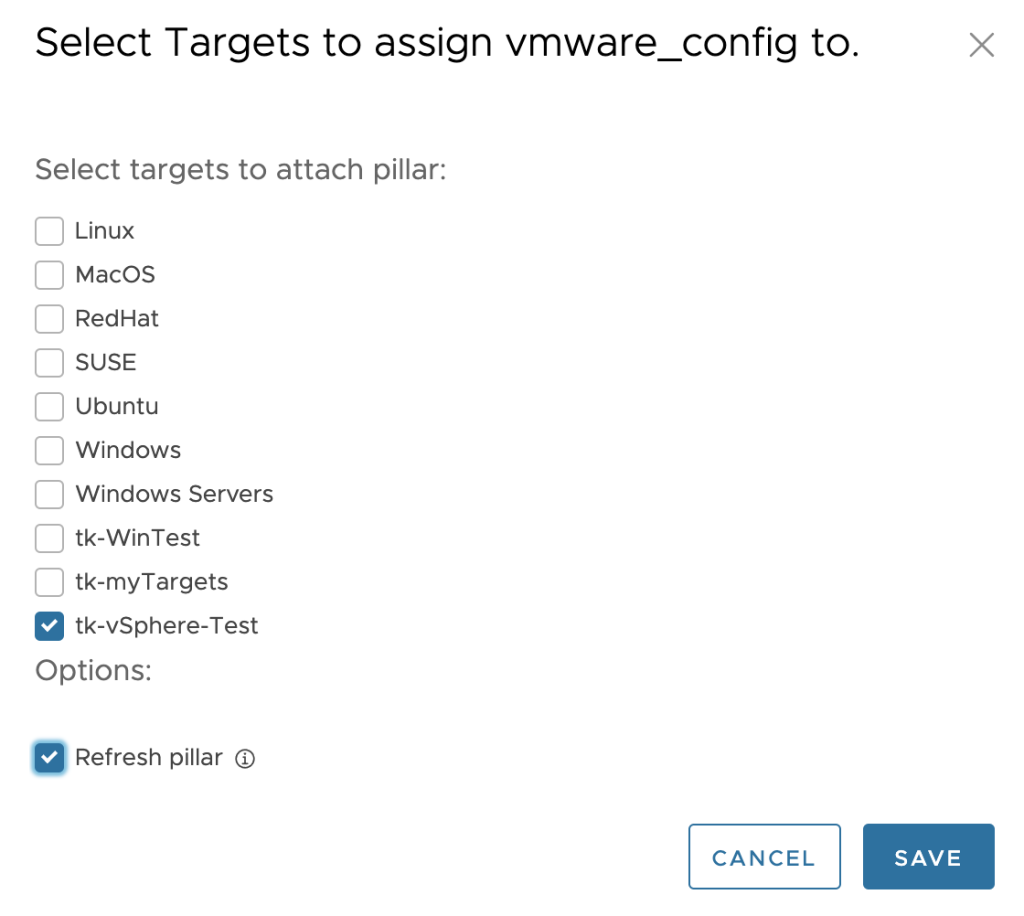
Step 2: Update the target, in my use case the dedicated minion, to include the data in this pillar.
Step 3: With the following command executed on the target Salt minion we can check if the pillar has been applied and the minion has all the needed information.
[root@tk-lin-131 ~]# salt-call pillar.items
local:
----------
vmware_config:
----------
host:
vc-demo.xxx.xxx
password:
xxxxxxx
user:
Administrator@demo.local
Step 4: Install the Salt Extension Modules for VMware on the minion with the following command as described in the Quickstart.
$ salt-call pip.install saltext.vmware
In case you receive an error pointing to an outdated pip version, simply run pip upgrade on the minion:
python3 -m pip install --upgrade pip
Step 5: Check if the modules are available on your minion (the output is truncated to display only the relevant modules):
[root@tk-lin-131 ~]# salt-call --local sys.list_modules
local:
- nsxt_compute_manager
- nsxt_ip_blocks
- nsxt_ip_pools
- nsxt_license
- nsxt_manager
- nsxt_policy_segment
- nsxt_policy_tier0
- nsxt_policy_tier1
- nsxt_transport_node
- nsxt_transport_node_profiles
- nsxt_transport_zone
- nsxt_uplink_profiles
- vmc_dhcp_profiles
- vmc_direct_connect
- vmc_distributed_firewall_rules
- vmc_dns_forwarder
- vmc_nat_rules
- vmc_networks
- vmc_public_ip
- vmc_sddc
- vmc_sddc_host
- vmc_security_groups
- vmc_security_rules
- vmc_vpn_statistics
- vmware_cluster
- vmware_cluster_drs
- vmware_cluster_ha
- vmware_datacenter
- vmware_datastore
- vmware_dvswitch
- vmware_esxi
- vmware_folder
- vmware_license_mgr
- vmware_tag
- vmware_vm
Step 6: Check if the minion is successfully connecting to the vCenter specified in the pillar and if the modules are working as expected (output truncated for visibility):
[root@tk-lin-131 ~
]# salt-call vmware_datacenter.list
local:
- Demo-Datacenter
[root@tk-lin-131 ~
]# salt-call vmware_cluster.get cluster_name=HP-Cluster datacenter_name=Demo-Datacenter
local:
----------
drs:
----------
advanced_settings:
----------
default_vm_behavior:
fullyAutomated
enable_vm_behavior_overrides:
True
enabled:
True
vmotion_rate: 3
drs_enabled:
True
Step 7: Now we can start creating Salt state files which will be integral and prescriptive part of our configuration management.
The following state file is just a very simple example. It configures few security settings on all my ESXi hosts in the vCenter we have specified in the pillar in step 1.
set_sec_config_max_days:
module.run:
- name: vmware_esxi.get_advanced_config
- config_name: Security.PasswordMaxDays
- config_value: 99998
set_sec_config_unlock_time:
module.run:
- name: vmware_esxi.get_advanced_config
- config_name: Security.AccountUnlockTime
- config_value: 899
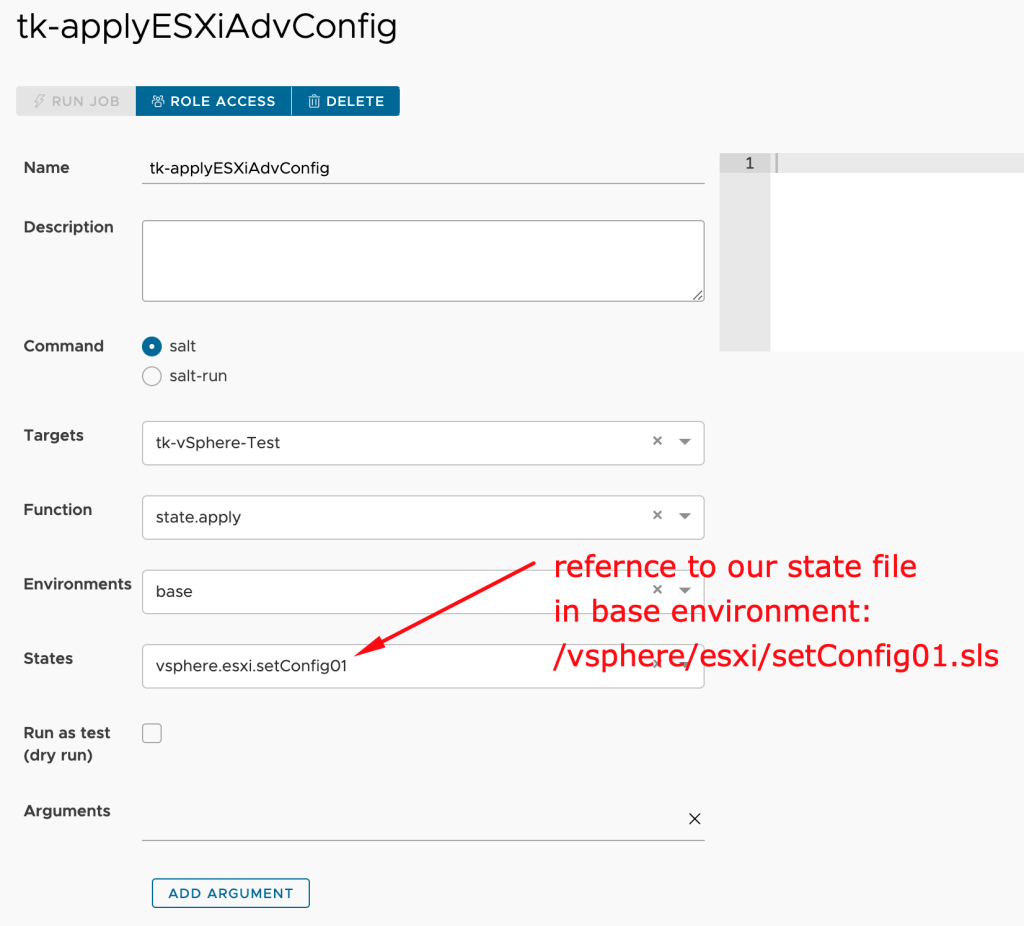
Step 8: We can apply this state file to our dedicated minion using e.g. a Salt job as shown in the next picture.
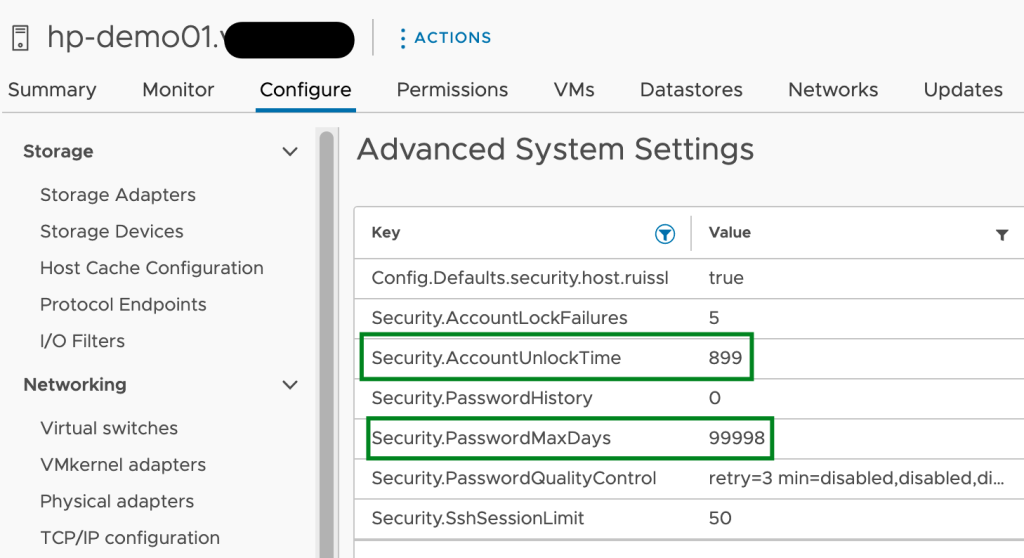
Step 9: In the last step we can finally check the outcome. We can use the corresponding get command on our minion or just review the settings in vCenter.
[root@tk-lin-131 ~]# salt-call vmware_esxi.get_advanced_config config_name=Security
local:
----------
hp-demo01.xxx.yyy:
----------
Security.AccountLockFailures:
5
Security.AccountUnlockTime:
899
Security.PasswordHistory:
0
Security.PasswordMaxDays:
99998
Security.PasswordQualityControl:
retry=3 min=disabled,disabled,disabled,7,7
Some final notes
Please note that after changing the state file it may take Salt a few seconds to reflect that change in the virtual file system. If you run a Salt job immediately after changing the state file, Salt may use the “old version”.
In my example, I have used an execution module. Usually, you would use a state module to check a setting and only apply a configuration if there is a deviation. At the moment of writing this post, the ESXi state module does not support checking Advanced Configuration. Since this is an Open Source module anyone can try to implement it:-)
Stay safe
Thomas – https://twitter.com/ThomasKopton

1 Comment