One of the great things about an all-encompassing Private Cloud solution like VMware Cloud Foundation (VCF) is how much it automates for you. From automatically installing or updating VCF Operations Cloud Proxies to managing critical passwords like the root user’s within the VCF Fleet Manager, VCF aims to streamline your operations. But what happens when you actually need that root password? How do you retrieve it?
In this post, I’ll walk you through the process of accessing passwords stored in the VCF Fleet Manager’s secure vault, specifically demonstrating with the root user for a VCF Operations Cloud Proxy.
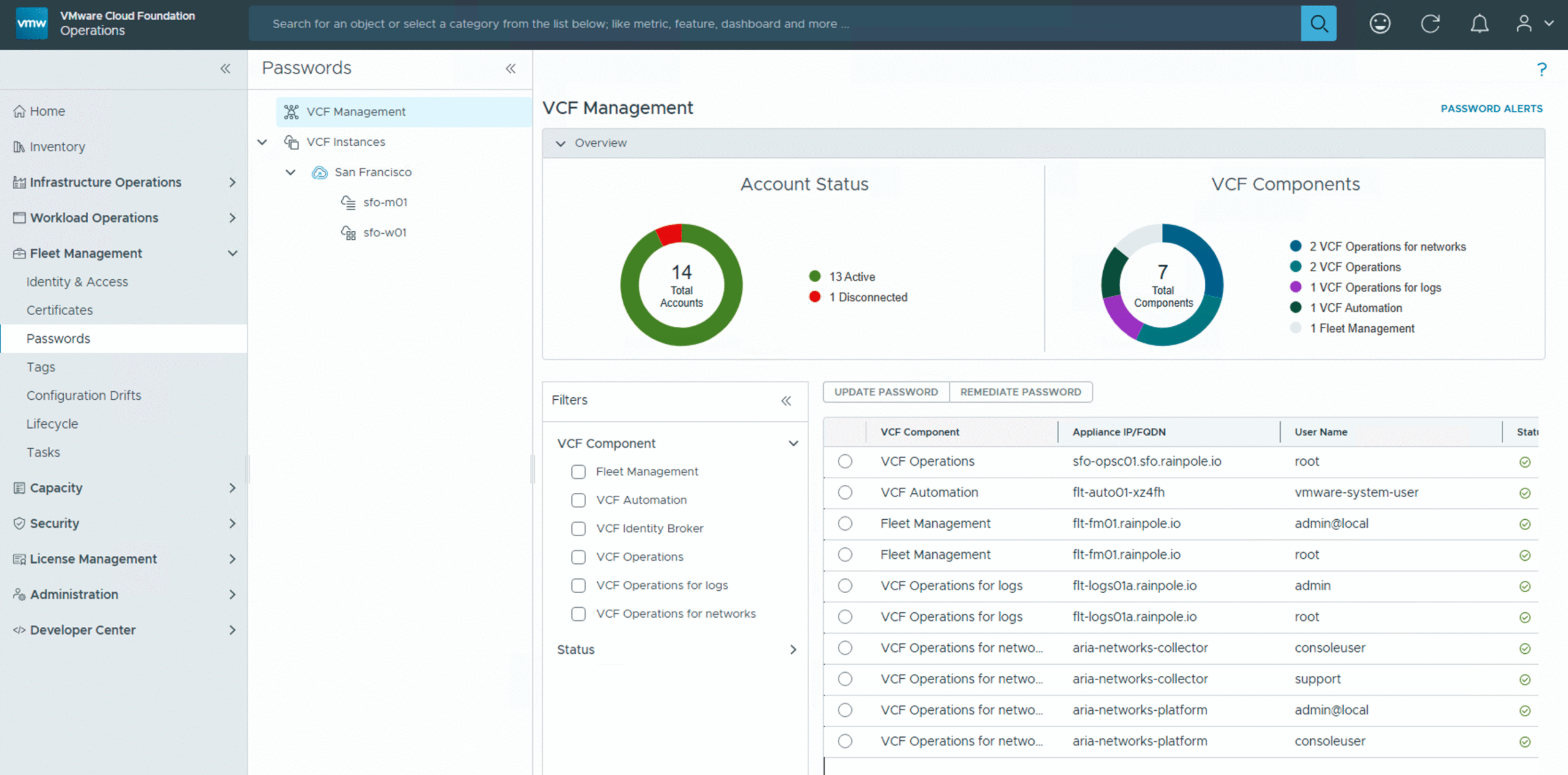
VCF Fleet Management Passwords
Within the VCF Fleet Manager, Fleet Management Passwords is VCF’s answer to automated, secure credential handling. It centralizes, generates, and manages critical passwords—like those for VCF Operations Cloud Proxies—in a protected vault, reducing manual effort and bolstering security across your private cloud.
While the VCF Fleet Manager handles password management for crucial components behind the scenes, you won’t typically “retrieve” existing plaintext passwords directly from its interface. Instead, the Fleet Management Passwords feature is where you proactively manage these credentials. This means you can update or remediate passwords when necessary. If you need to regain access to a system whose password is managed by VCF, it involves a specific REST API based process, which is what we’ll explore – not simply pulling it from a vault.
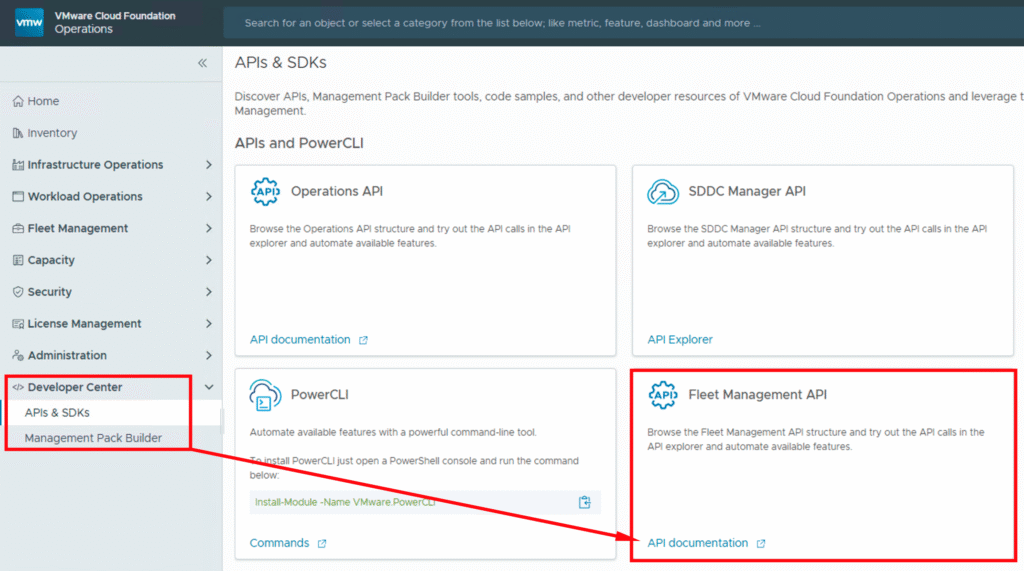
Fleet Management API
Moving beyond manual clicks in the UI, the VCF Fleet Management API is your gateway to unparalleled automation. It exposes the capabilities of the Fleet Manager through a set of programmatic endpoints, allowing you to script complex workflows and integrate VCF management into your existing automation frameworks.
In the next screenshot we can see how to access the VCF Fleet Management Swagger UI.
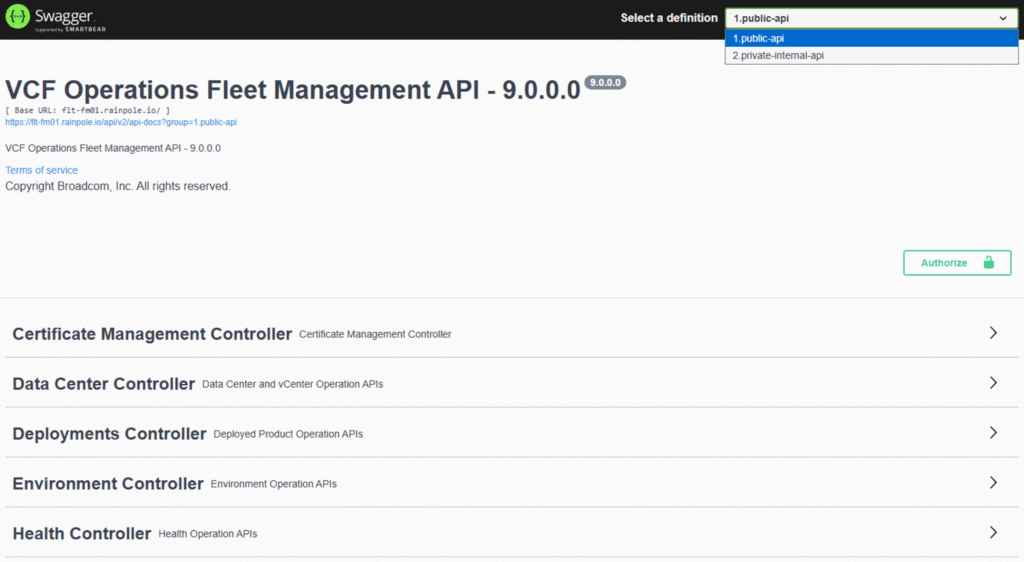
In the API Explorer we can choose between the public and the private API, as shown in the following screenshot.
Retrieving Password
The process for retrieving a password stored in VCF’s secure vault – specifically, the root user for our VCF Operations Cloud Proxy in this example – involves two three phases:
- Authorization
- Retrieving the vmid of the stored credentials
- Retrieving the decrypted password
Authorization
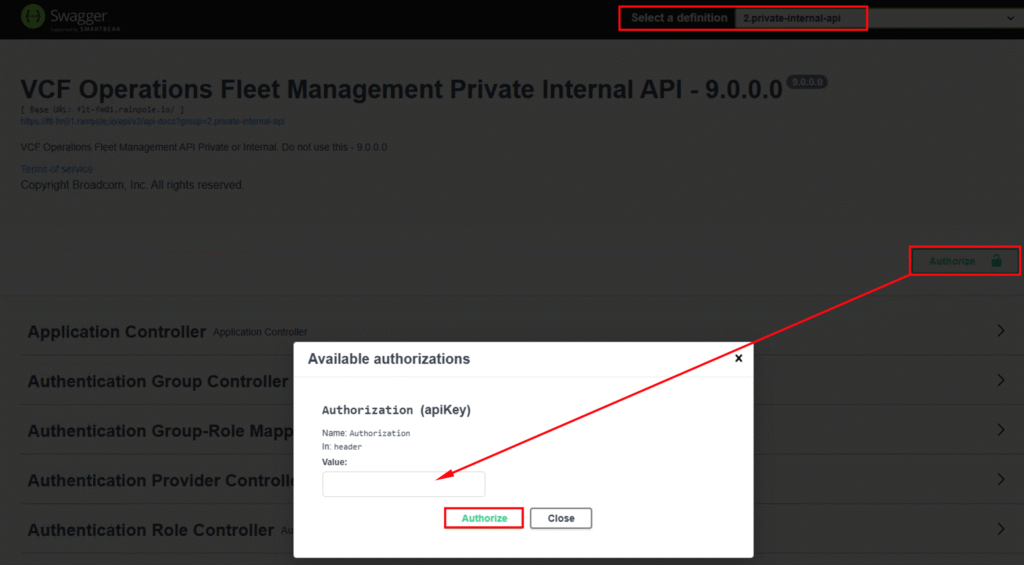
Authorization in the Swagger UI is a quick step. Clicking the appropriate button opens a dialog window expecting Base64 encoded Basic Auth. You’ll need to encode your User:Password combination and enter it as a Basic xxxxxxx string, as shown in the example below. Important Note: We are operating within the private-internal-api here.
admin@local:VMware123!
Basic YWRtaW5AbG9jYWw6Vk13YXJlMTIzIQ==The next screenshot shows the Authorization in the Swagger UI.
Get List of Passwords
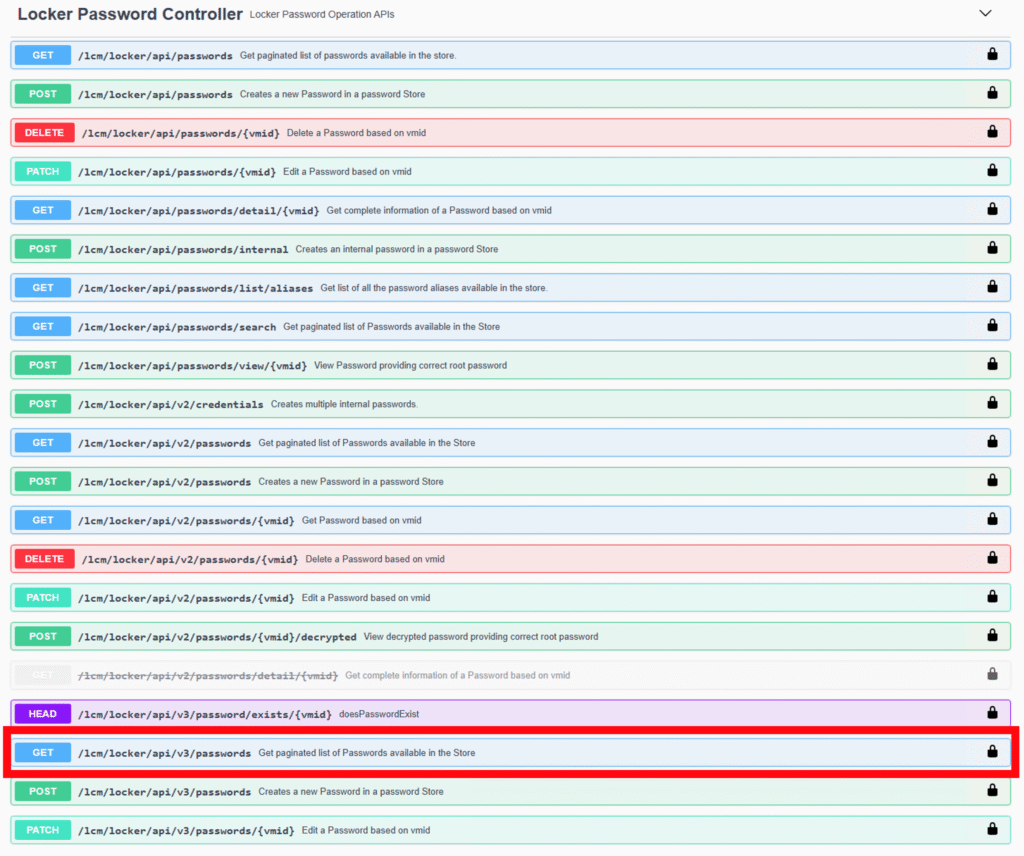
Next, we need to fetch the list of available credentials and locate our Cloud Proxy within it to obtain the vidm. This ID is essential for the final step.
In my lab, as of this post, I’m running the brand new VCF 9.0.1 version. The REST call we’ll be using can be found in the v3 section of the Locker Password Controller. The next image shows the GET call.
Of course, we can use Postman or simply curl for this, as shown here:
curl -X GET "https://flt-fm01.rainpole.io/lcm/locker/api/v3/passwords?limit=10" -H "accept: application/json" -H "Authorization: Basic YWxxxIQ=="Now, we’ll search through the returned JSON body to find our Cloud Proxy. The vidm will be one of the key-value pairs within its entry.
{
"vmid": "b4b63007-6e32-4462-9b0f-b9330e307eaf",
"alias": "VCF-sfo-opsc01.sfo.rainpole.io-rootUserPassword",
"userName": "root",
"passwordDescription": null,
"type": "node",
"status": "active",
"createdOn": 1753204380982,
"lastUpdatedOn": 1753204380982,
"lastValidatedOn": null,
"reference": {
"envId": "b5dcc1a4-8d66-4e83-be24-ef4180b7dd27",
"envName": "b5dcc1a4-8d66-4e83-be24-ef4180b7dd27",
"productId": "vrops",
"hostName": "sfo-opsc01.sfo.rainpole.io",
"ip": "10.11.10.38",
"nodeType": "cloudproxy",
"referenceId": "be49027a-16c8-469a-9285-3ad93f2d62ce"
}Decode Password
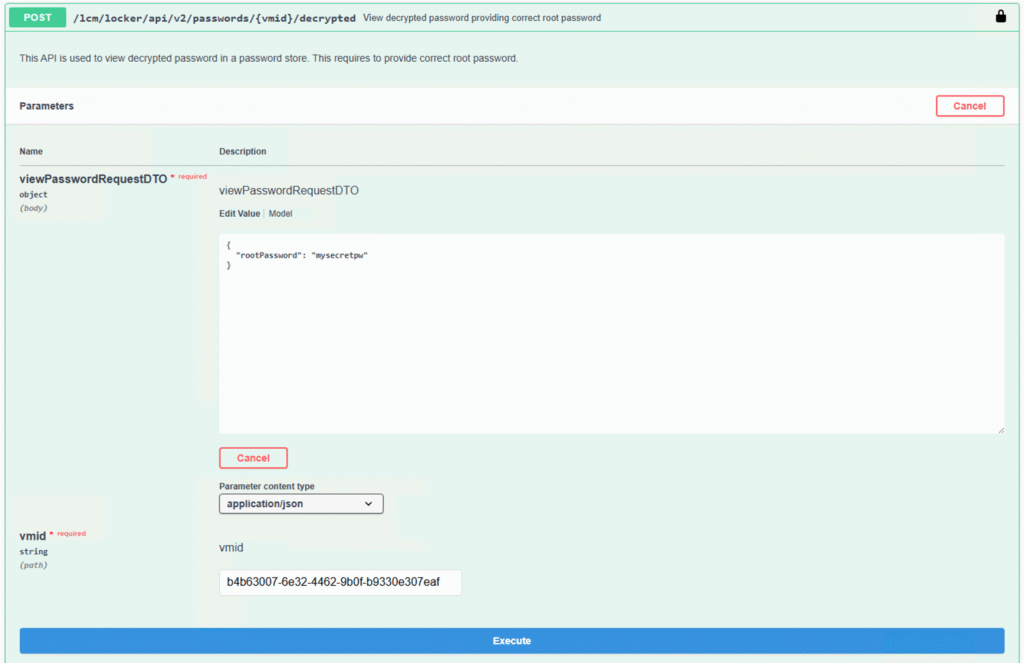
The final step is to call the /lcm/locker/api/v2/passwords/{vmid}/decrypted endpoint. This is a POST call that expects the password’s vmid as a URL parameter and the Fleet Manager’s root password in the JSON body. The next screenshot shows this call in Swagger.
And again as curl command.
curl -X POST "https://flt-fm01.rainpole.io/lcm/locker/api/v2/passwords/b4b63007-6e32-4462-9b0f-b9330e307eaf/decrypted" -H "accept: application/json" -H "Authorization: Basic YWRtaW5AbG9jYWw6Vk13QHJlMSFWTXdAcmUxIQ==" -H "Content-Type: application/json" -d "{ \"rootPassword\": \"mysecretpw\"}"And voilà! Here’s our decrypted password for the Cloud Proxy’s root user in the JSON response body:
{
"passwordVmid": "b4b63007-6e32-4462-9b0f-b9330e307eaf",
"password": "i#M7rq0qqw234W@hz76456&g5VEKf3p"
}Stay safe.
Thomas – https://twitter.com/ThomasKopton