Recently I had to install and configure a SaltStack Master in my home lab and connect this master to my Aria Automation Config Cloud (aka SaltStack Config, i will use both names in this post) instance.
Even if the official documentation improved a lot, there are still some pitfalls, especially if you are not experienced with the Salt setup.
In this blog post you will see, step by step, the entire process of preparing CentOS 8, installing Salt components and configuring the master to join the Cloud RaaS instance.
My new SaltStack Master will run on a CentOS 8 box:
4.18.0-348.2.1.el8_5.x86_64 #1 SMP
Step 1 – Prepare CentOS 8
The first thing you need to ensure is, that the firewall is not blocking the Salt master ports.
[root@saltmaster02 ~]# firewall-cmd --permanent --add-port=4505-4506/tcp success [root@saltmaster02 ~]# firewall-cmd --reload success
You can find the details on the official page of the salt project: https://docs.saltproject.io/en/latest/topics/tutorials/firewall.html
You also need to ensure that the gcc package is installed, if it is not available, simply run:
sudo yum install gcc python3-devel
Step 2 – Install Salt on your Salt master
You must install the Salt master service and Salt minion service plus some few more packages if needed on the Salt master. The following instructions install the latest Salt release on CentOS 8 (RHEL 8).
In the Salt master’s terminal, run the following commands to install the Salt Project repository and key:
sudo rpm --import https://repo.saltproject.io/py3/redhat/8/x86_64/latest/SALTSTACK-GPG-KEY.pub curl -fsSL https://repo.saltproject.io/py3/redhat/8/x86_64/latest.repo | sudo tee /etc/yum.repos.d/salt.repo
Run sudo yum clean expire-cache. Install the salt-minion service and salt-master service on your Salt master:
sudo yum install salt-master sudo yum install salt-minion # Optional packages sudo yum install salt-ssh sudo yum install salt-syndic sudo yum install salt-cloud sudo yum install salt-api
Enable and start service for salt-minion, salt-master, or other Salt components:
sudo systemctl enable salt-master && sudo systemctl start salt-master sudo systemctl enable salt-minion && sudo systemctl start salt-minion sudo systemctl enable salt-syndic && sudo systemctl start salt-syndic sudo systemctl enable salt-api && sudo systemctl start salt-api
See the Salt Install guide for information about installing Salt on other operating systems.
Step 3 – Create initial master configuration
Create a master.conf file in the /etc/salt/minion.d directory. In this file, set the Salt master’s IP address to point to itself:
master: localhost
Restart the Salt master service and Salt minion service (the services have been enabled in the previous step):
sudo systemctl restart salt-master sudo systemctl restart salt-minion
Step 4 – Install and configure the Master Plugin
After you install Salt on your om-premises infrastructure, you must install and configure the Master SSEAPE Plugin, which enables your Salt masters to communicate with Aria Automation Config (SaltStack Config) Cloud.
To install and configure the Master PSSEAPE Plugin you first need to install the required Python libraries. Login to your local master and run:
sudo pip3 install pyjwt sudo pip3 install pika
Download the latest Master Plugin wheel from Customer Connect. You will find the file in the package highlighted in the following picture.

The Master Plugin is included in the Automated Installer .tar.gz file. After you download and extract the .tar.gz file, you can find the Master Plugin in the sse-installer/salt/sse/eapi_plugin/files directory.
Put the wheel file into your /root directory and install the Master Plugin by manually installing the Python wheel. Use the following example commands, replacing the exact name of the wheel file:
sudo pip3 install SSEAPE-file-name.whl --prefix /usr
Verify that the /etc/salt/master.d directory exists, create it if needed.
Run the following command to generate the master configuration file.
sudo sseapi-config --all > /etc/salt/master.d/raas.conf
If running this command causes an error, see Troubleshooting SaltStack Config Cloud.
Restart the Salt master service.
sudo systemctl restart salt-master
Step 5 – Generate an API token
Before you can connect your Salt master to Aria Automation Config Cloud, you must generate an API token using the Cloud Services Console. This token is used to authenticate your Salt master with VMware Cloud Services.
NOTE: You must have the same role(s) as the role(s) you are configuring for the token. So for example if you are assigning the Organization-Administrator role to the new token you must be Organization-Administrator as well! Please also see: https://docs.vmware.com/en/VMware-Cloud-services/services/Using-VMware-Cloud-Services/GUID-E2A3B1C1-E9AD-4B00-A6B6-88D31FCDDF7C.html
To generate an API token:
On the Cloud Services Console toolbar, click your user name and select My Account > API Tokens.
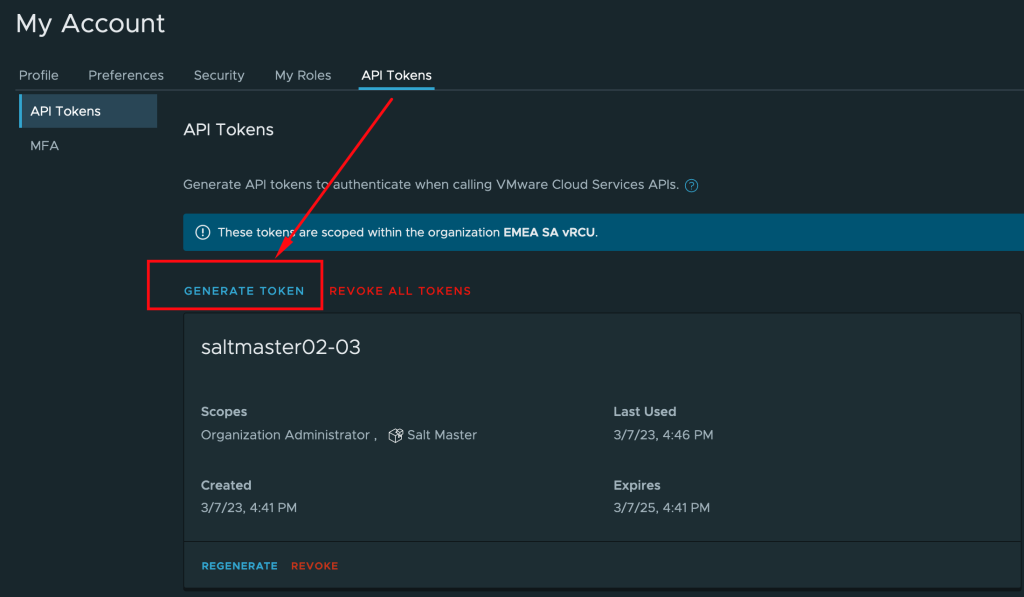
Enter a name for the token.
Select the token’s Time to Live (TTL). The default duration is six months. Note: A non-expiring token can be a security risk if compromised. If this happens, you must revoke the token.
Define scopes for the token. To access the Aria Automation Config Cloud service, you must select the Organization Admin or Organization Owner roles as well as the Salt Master Service Role.
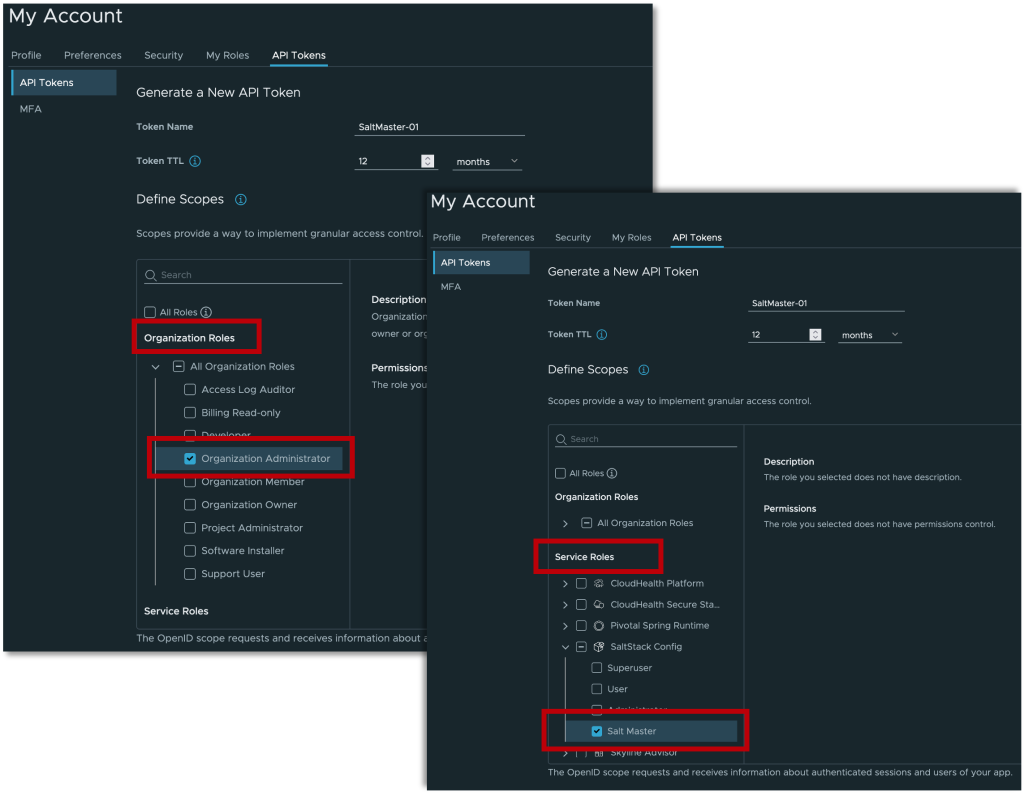
(Optional) Set an email preference to receive a reminder when your token is about to expire.
Click Generate and the newly generated API token will appear in the Token Generated window.
Save the token value to a secure location. After you generate the token, you will only be able to see the token’s name on the API Tokens page, not the token value itself. To regenerate the token, click Regenerate.
Step 6 – Connect your Salt master to Aria Automation Config (SaltStack Config) Cloud
After you generated an API token, you use it to connect your Salt master to Aria Automation Config Cloud.
To connect your Salt master first set a env variable to store the API token you have created in the previous step:
export CSP_API_TOKEN=<api token value>
Run the sseapi-config join command to connect your Salt master to Aria Automation Config Cloud. You have to replace the ssc-url and csp-url values with your region-specific URLs. See the following table for the region-specific URLs.
| Region name | SSC URL | CSP URL |
| US | https://ssc-gateway.mgmt.cloud.vmware.com | https://console.cloud.vmware.com |
| DE (Germany) | https://de.ssc-gateway.mgmt.cloud.vmware.com | https://console.cloud.vmware.com |
| IN (India) | https://in.ssc-gateway.mgmt.cloud.vmware.com | https://console.cloud.vmware.com |
Run the sseapi-config join command:
sudo sseapi-config join --ssc-url <SSC URL> --csp-url <CSP URL>
In my example the command will be:
sseapi-config join --ssc-url https://ssc-gateway.mgmt.cloud.vmware.com --csp-url https://console.cloud.vmware.com
If you need to redo the joining process, re-run the sseapi-config join command and pass the flag --override-oauth-app.
sseapi-config join --ssc-url <SSC URL> --csp-url <CSP URL> --override-oauth-app
The --override-oauth-app flag deletes the OAuth app used to get an access token and recreates it.
Restart the Salt master service.
systemctl restart salt-master
“Repeat this process for each Salt master. Note: After you connect each Salt master to Aria Automation Config Cloud, you can delete the API token. It is only required for connecting your Salt masters.
After you run the sseapi-config command, an OAuth app is created in your Organization for each Salt master. Salt masters use the OAuth app to get an access token which is appended to every request to Aria Automation Config Cloud. You can view the details of the OAuth app by selecting Organization > OAuth Apps.
The command also creates pillar data called CSP_AUTH_TOKEN on the Salt master. Pillars are structures of data stored on the Salt master and passed through to one or more minions that have been authorized to access that data. The pillar data is stored in /srv/pillar/csp.sls and contains the client ID, the secret, your organization ID, and CSP URL. If you need to rotate your secret, you can re-run the sseapi-config join command.“
Example pillar data:
CSP_AUTH_TOKEN: csp_client_id: kH8wIvNxMJEGGmk7uCx4MBfPswEw7PpLaDh csp_client_secret: ebH9iuXnZqUOkuWKwfHXPjyYc5Umpa00mI9Wx3dpEMlrUWNy95 csp_org_id: 6bh70973-b1g2-716c-6i21-i9974a6gdc85 csp_url: https://console.cloud.vmware.com
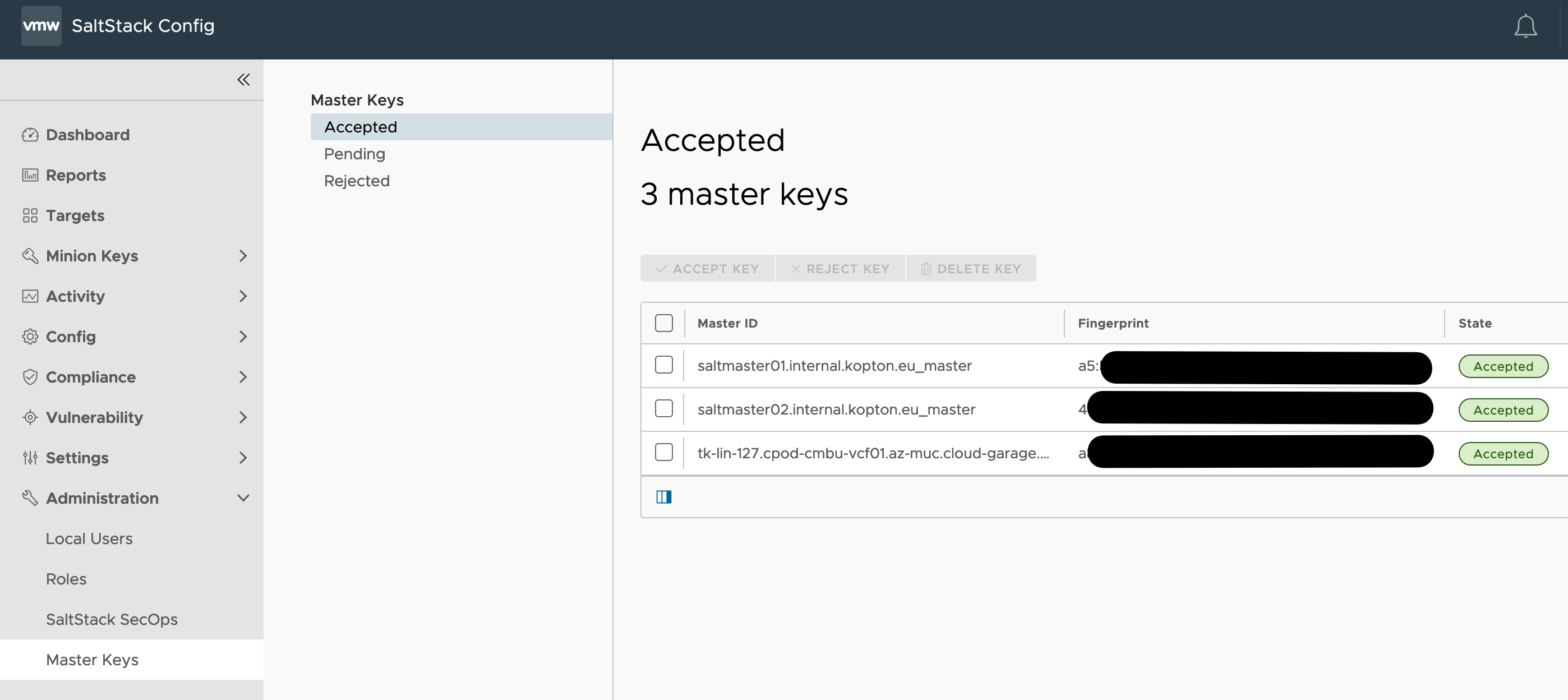
Step 7 – Accept Salt master keys
After you connected your Salt master(s) to Aria Automation Config Cloud, you must accept the Salt master’s key in the Aria Automation Config Cloud user interface.
You must have the Superuser role in SaltStack Config Cloud to accept the Salt master’s key.
To accept the Salt master’s key:
- Log in to the SaltStack Config Cloud user interface.
- From the top left navigation bar, click the Menu, then select Administration to access the Administration workspace. Click the Master Keys tab.
- Check the box next to the master key to select it. Then, click Accept Key.
- If you already connected your Salt minions to your Salt master, an alert appears indicating that you have pending minion keys to accept. To accept these minion keys, go to Minion Keys > Pending.
- Check the boxes next to your minions to select them. Then, click Accept Key.

You can verify that your Salt master and Salt minions are communicating by running a test.ping command in the Aria Automation Config Cloud user interface.
Stay safe.
Thomas – https://twitter.com/ThomasKopton