Recently, I was asked if there’s a way to programmatically read the results of a compliance check for specific ESXi hosts in VMware Aria Operations. The use case here is that the customer wants to utilize these compliance results in an automated workflow.
This is an interesting question that highlights the growing need for automation and integration in IT operations. As environments become more complex and compliance requirements more stringent, the ability to programmatically access and act on compliance data becomes increasingly valuable.
The Challenge
VMware Aria Operations provides robust compliance checking capabilities, including predefined benchmarks for various standards and the ability to create custom compliance rules. However, accessing this data programmatically for use in external workflows isn’t straightforward out of the box.
Potential Solution
While VMware Aria Operations doesn’t have a built-in feature specifically for this purpose, there are a two approaches which combined deliver the solution:
- Views: Create a custom View focusing on the compliance data you need.
- REST API: Use the API to extract this information.
Report
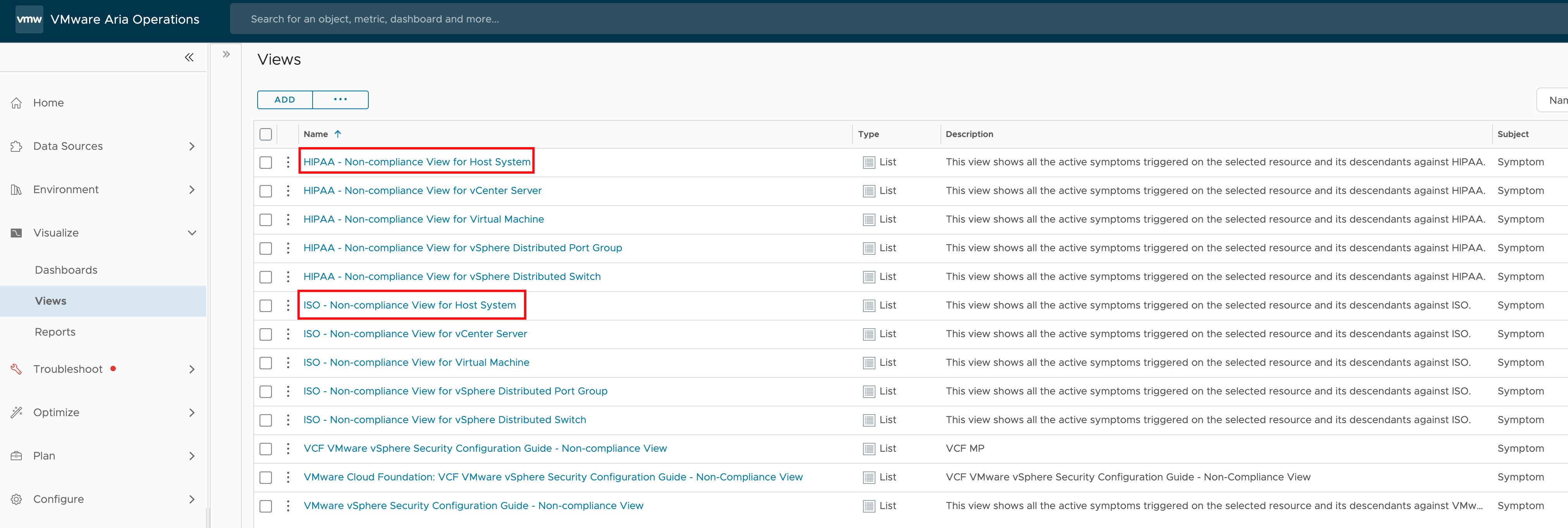
I won’t be showing how to create an Aria Operations Views. For simplicity, we’ll use an existing compliance focused view. It’s generally a good idea to use existing views as templates and customize them to meet specific needs, thereby creating tailored views.
To check the compliance status of ESXi hosts, you can use the following out-of-the-box views. These views are part of the Compliance Packs.
Using these predefined views simplifies the process of monitoring and ensuring that your ESXi hosts meet the required compliance standards. The Compliance Packs include various benchmarks and alert definitions that help you identify non-compliant objects and take corrective actions.
For more detailed information on configuring and using these views, refer to the VMware Aria Operations documentation on compliance monitoring and reporting.
REST API Call
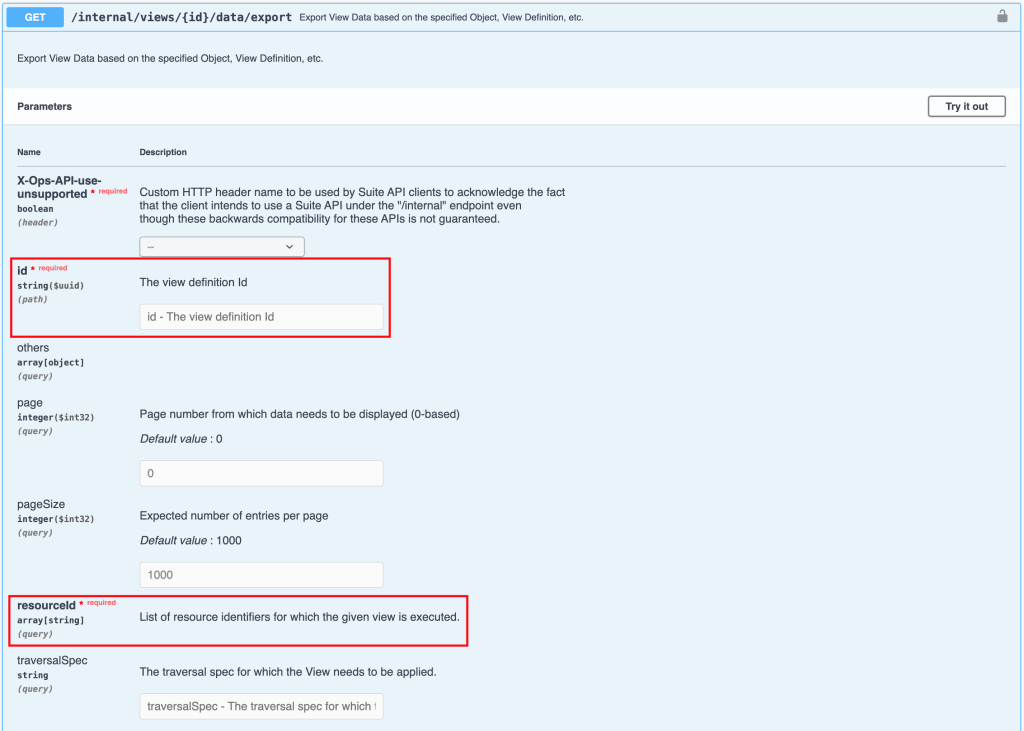
How can we access the views programmatically? The internal section of the REST API contains a suitable call for this purpose:
GET /internal/views/{id}/data/exportThis call allows you to export view data based on the specified object, view definition, etc.
To obtain the compliance status for selected ESXi hosts, we need to provide the REST call with the appropriate parameters, as shown in the following image.
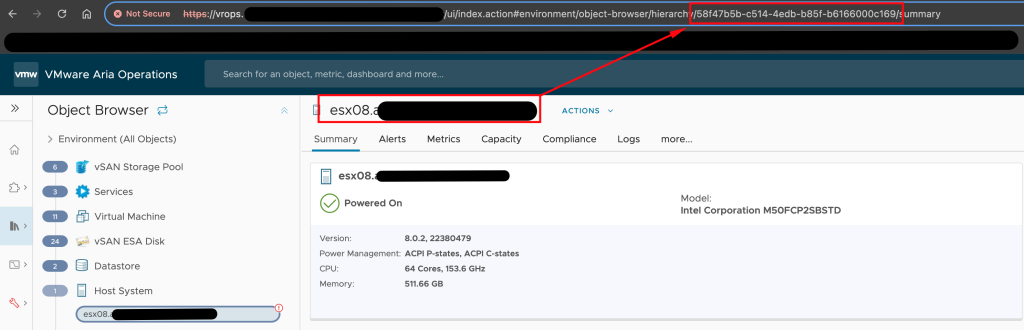
Now, we just need to determine the ID of the view and the ESXi hosts we are interested in. This can be done, for example, through the Aria Operations UI. The following image shows the ID of a specific view and the subsequent one of an ESXi host.

Now, we just need to construct and send the REST call. In Postman, it looks like this (IDs have to be replaces by your own ID, of course):

You can also run the call for multiple resources at once, simply add more resourceId parameters.
And this is how the curl command looks like (token and IDs truncated for better visibility):
curl --location 'https://vrops/suite-api/internal/views/e5xxxc6/data/export?resourceId=58xxx69' \
--header 'Authorization: vRealizeOpsToken f0xxxb0' \
--header 'X-vRealizeOps-API-use-unsupported: true' \
--header 'Accept: application/json'The output JSON which you have to parse programmatically has a very simple structure. All resources specified using their resourceId are within the rows array and every column of the view is represented by a cell in the JSON:
"rows": [
{
"cells": {
"summary": false,
"1": "ALERT_CRITICALITY_LEVEL_WARNING",
"groupUUID": null,
"2": "ALERT_STATUS_ACTIVE",
"3": "esx08",
"4": "Host System",
"5": "THIS_RESOURCE",
"grandTotal": false,
"6": 1716459696194,
"objId": "ISO 27001-27002 - Integrity - Firewall is not configured for NTP service",
"objUUID": null
}
},
{
"cells": {
"summary": false,
"1": "ALERT_CRITICALITY_LEVEL_WARNING",
"groupUUID": null,
"2": "ALERT_STATUS_ACTIVE",
"3": "esx08",
"4": "Host System",
"5": "THIS_RESOURCE",
"grandTotal": false,
"6": 1716459696194,
"objId": "ISO 27001-27002 Active directory is not configured for Local Authentication",
"objUUID": null
}
},Stay safe.
Thomas