As you probably know vRealize Operations provides several symptom definitions based on message events as part of the vCenter Solution content OOTB. You can see some of them in the next picture. These events are used in alert definitions to raise vReaalize Operations alarms any time one of those events is triggered in any of …
vRealize Operations AMQP Integration using Webhooks
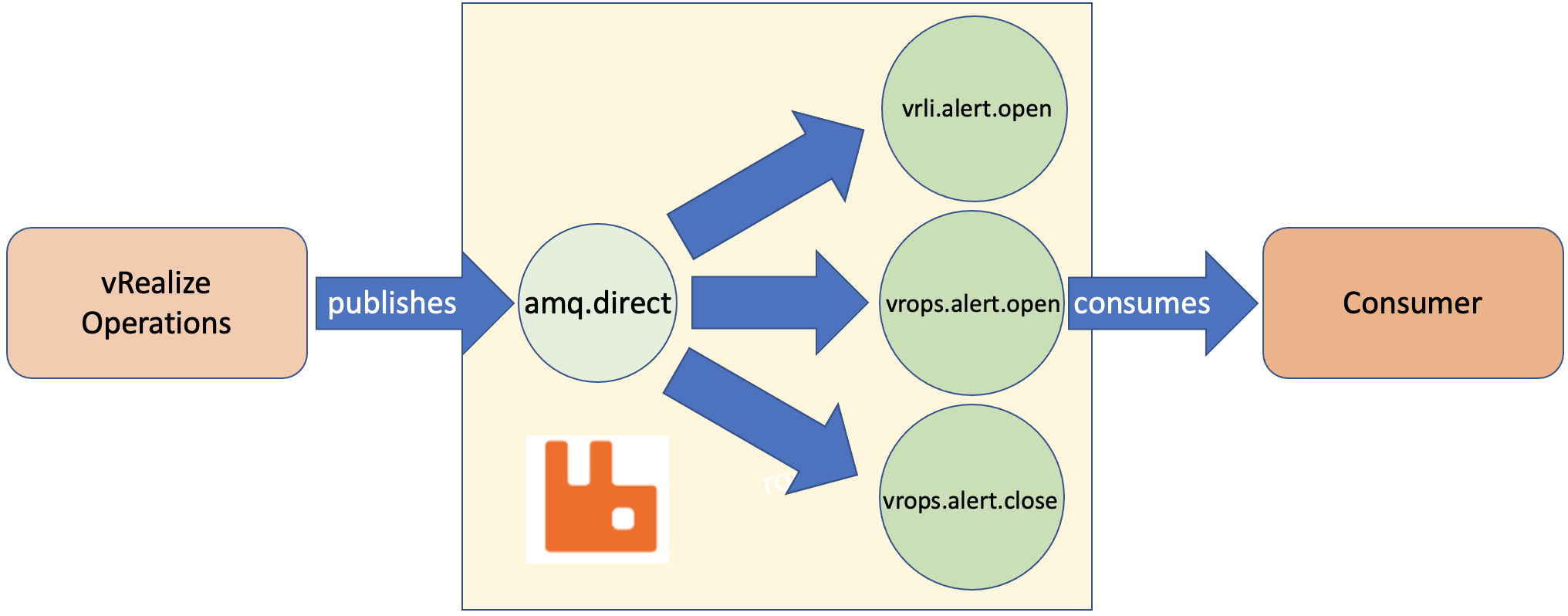
With the version 8.4 vRealize Operations introduced the Webhook Outbound Plugin feature. This new Webhook outbound plugin works without any additional software, the Webhook Shim server becomes obsolet. In this post, I will explain how to integrate vRealize Operations with an AMQP system. For this exercise, I have deployed a RabbitMQ server but the concept …
Wavefront by VMware and Log Ingestion
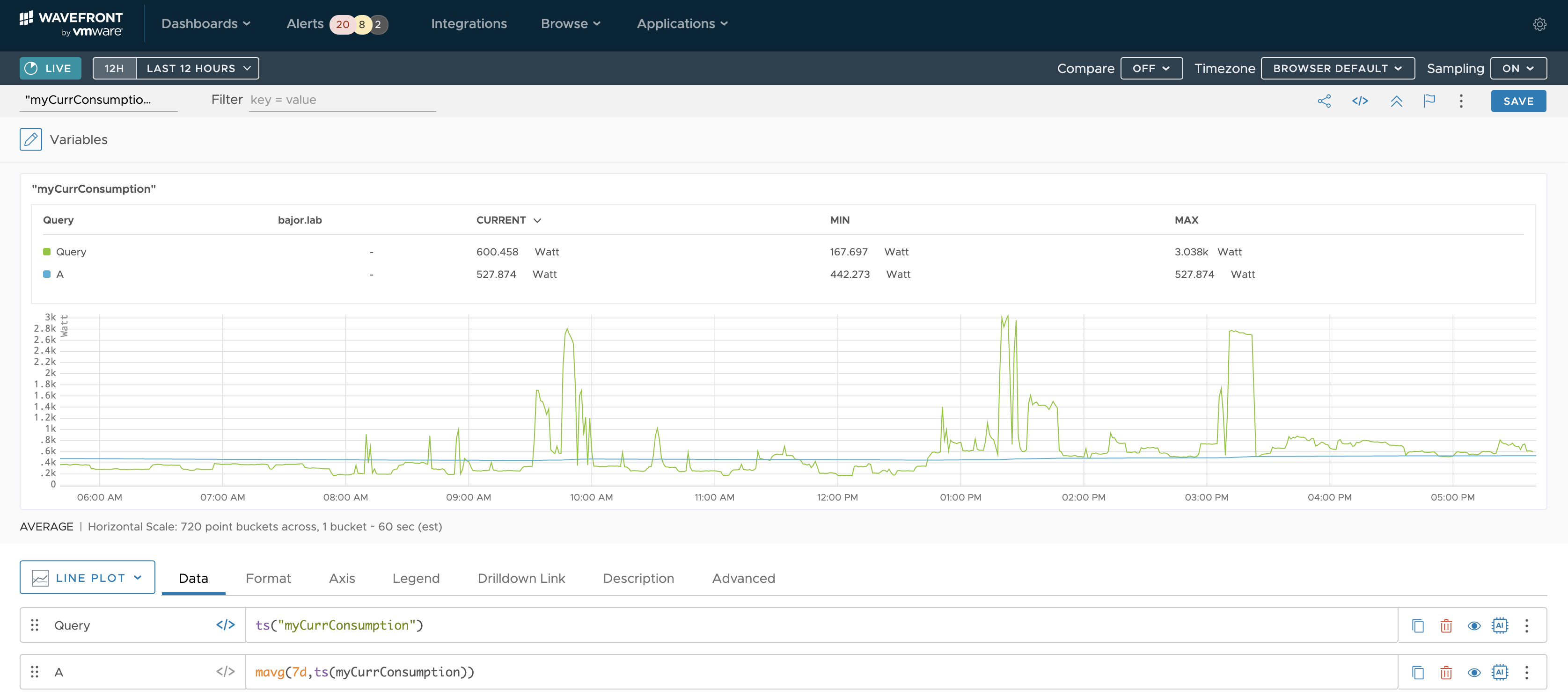
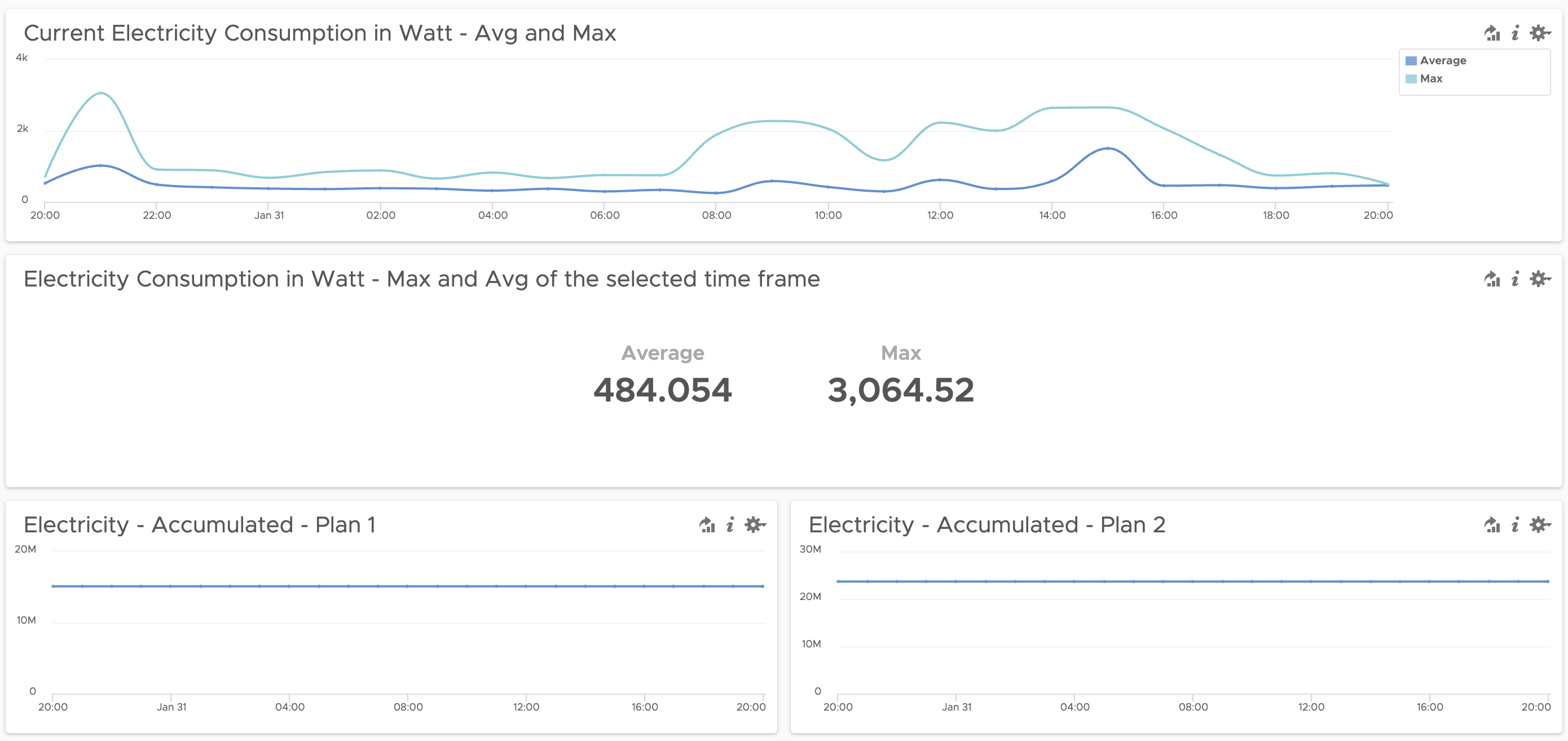
Motivation In my last post, I have described how to ingest power consumption data provided by the vzlogger project into vRealize Log Insight and how to extract the actual metrics from the log message. That setup is working since days as expected but the primary use case for vRealize Log Insight is intelligent logging and …
Energy Consumption Monitoring using SML Data and vRealize Log Insight
It all started with my last electricity bill. Shortly after I have recovered from the shock and made sure that I really do not have any aluminum smelter running in my basement, I decided, I need some kind of monitoring of my electric energy consumption. Insights into data is the first and probably most important step …
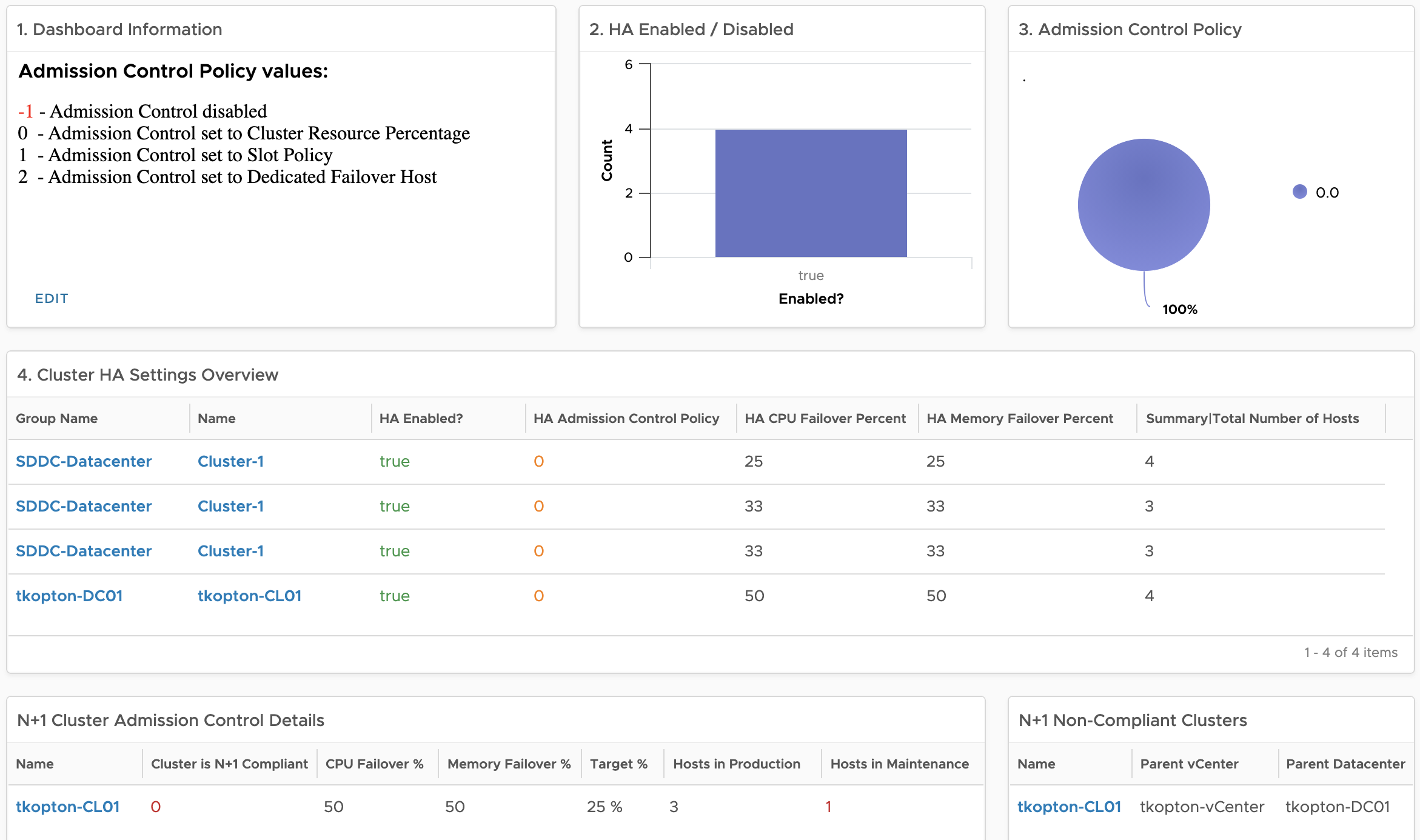
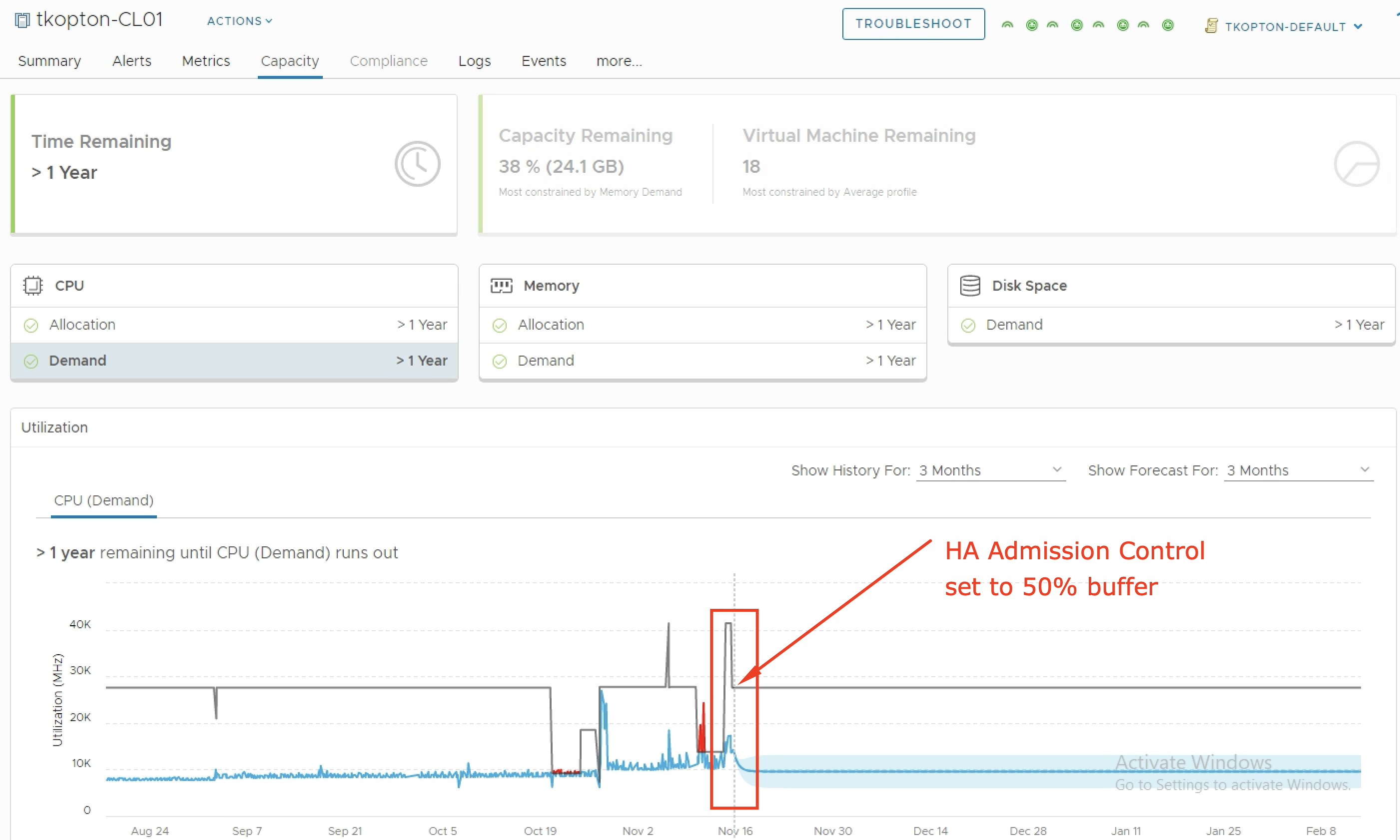
Monitoring vSphere HA and Admission Control Settings using vRealize Operations
vSphere High Availability (vSphere HA) and Admission Control ensure that sufficient resources are reserved for virtual machine recovery when a host fails. Usually, my customers are running their vSphere clusters in either N+1 or N*2 configurations reflected corresponding Admission Control settings In one of my previous blog posts, I have described how vRealize Operations helps with …
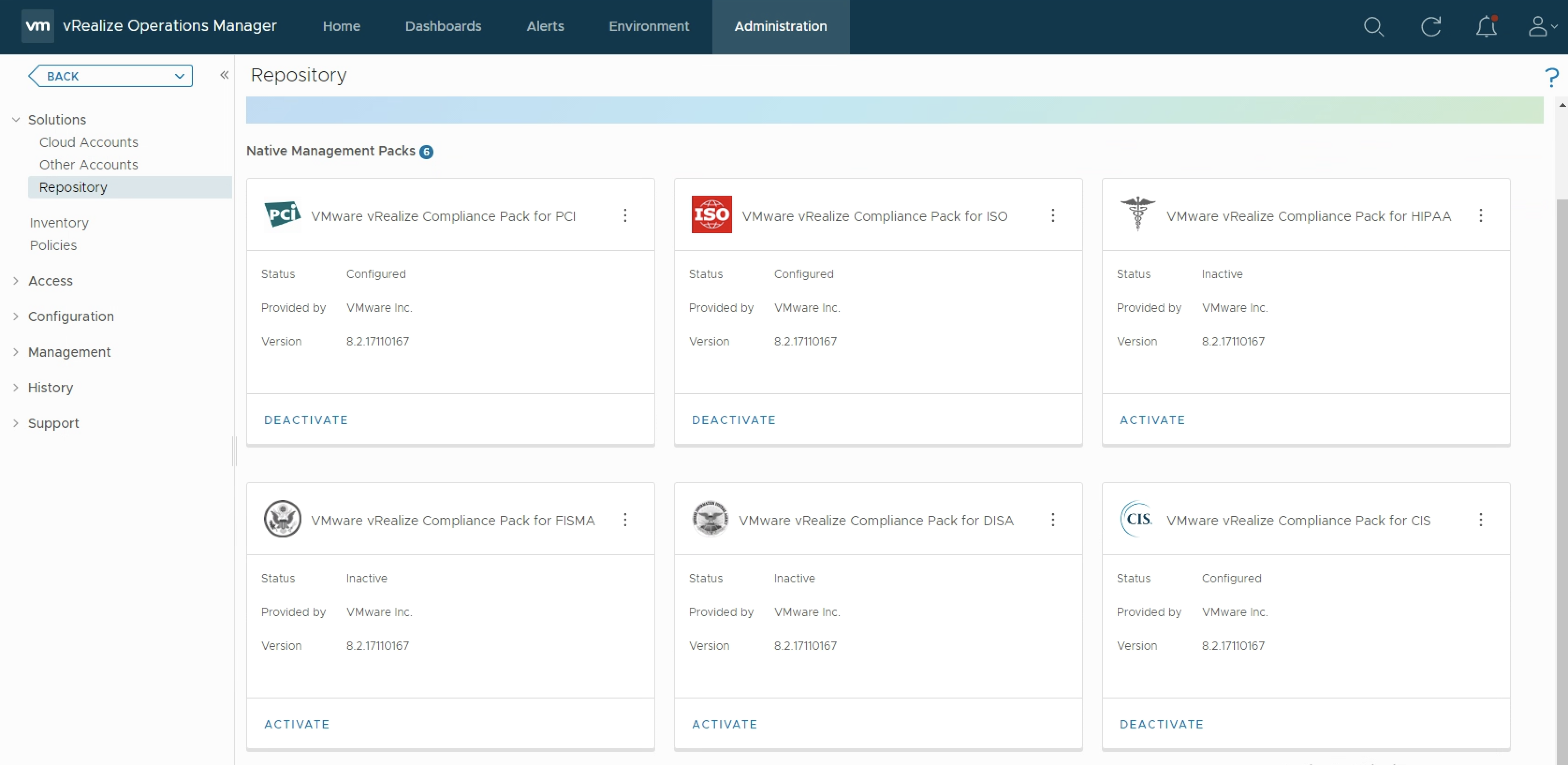
Custom Compliance Management using vRealize Operations
As you probably know vRealize Operations provides several Compliance Packs basically out-of-the-box (“natively”). A simple click on “ACTIVATE” in the “Repository” tab installs all needed components of the Compliance Pack and allows the corresponding regulatory benchmarks to be executed. “Regulatory benchmarks provide solutions for industry standard regulatory compliance requirements to enforce and report on the …
Capacity Management for n+1 and n*2 Clusters using vRealize Operations
When it comes to capacity management in vSphere environments using vRealize Operations customers are frequently asking for guidelines how to setup vROps to properly manage n+1 and n*2 ESXi clusters. Just as a short reminder, n+1 in context of a ESXi cluster means that we are tolerating (and are hopefully prepared for) the failure of …
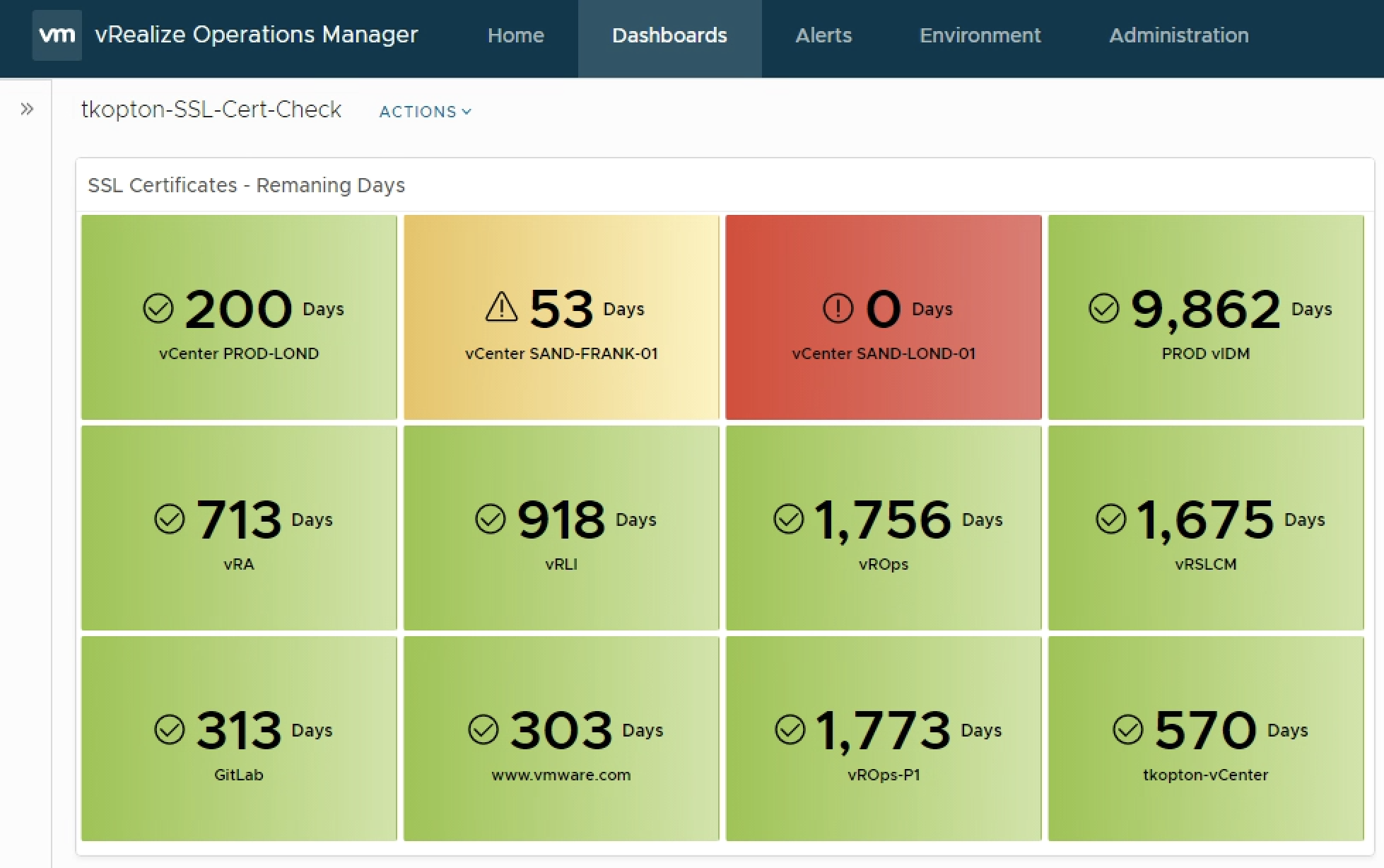
Checking SSL/TLS Certificate Validity Period using vRealize Operations Application Monitoring Agents
In my 2019 article “Checking SSL/TLS Certificate Validity Period using vRealize Operations and End Point Operations Agent” on VMware Cloud Management Blog (https://blogs.vmware.com/management/2019/05/checking-ssl-tls-certificate-validity-period-using-vrealize-operations-and-end-point-operations-agent.html) I have described how to check the remaining validity of SSL/TLS certificates. The method back then was to utilize the End Point Operations Agents. Since vRealize Operations 7.5 new Application Monitoring capabilities …
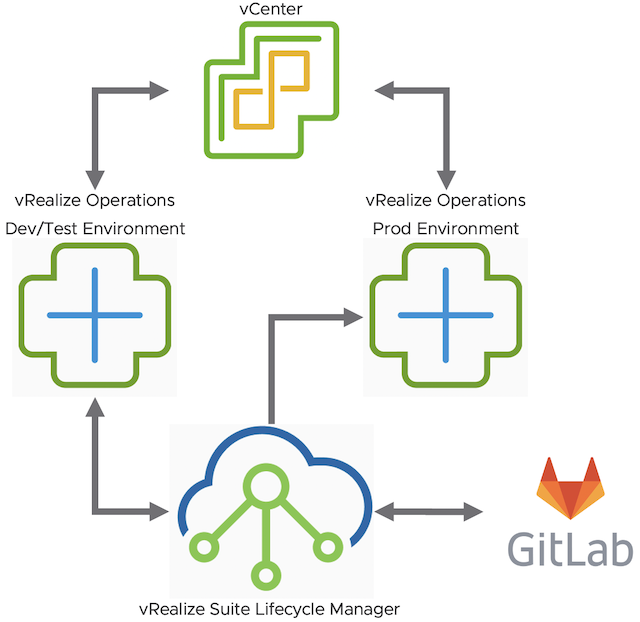
vRealize Operations Content Management – CD Pipeline – Part 1
vRealize Operations provide a wide range of content OOB. It gives the Ops teams a variety of dashboards, view, alerts etc. to run and manage their environments. Sooner or later, in most cases rather sooner than later, vROps users will create their own content. It might be completely new dashboards or maybe just adjusted alert …
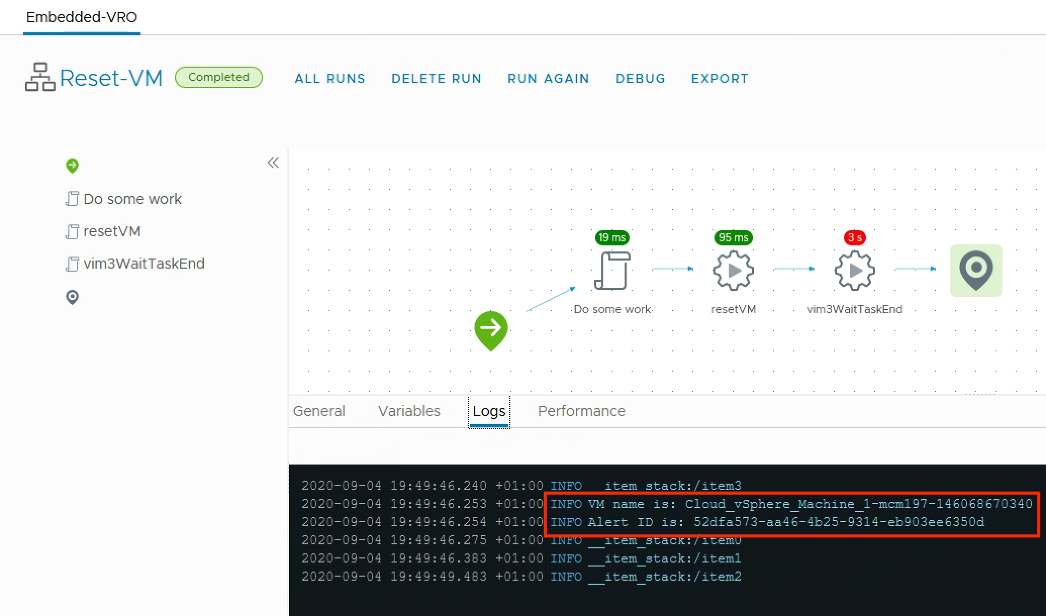
Self-Healing with vRealize Operations and vRealize Orchestrator
The vRealize Operations Management Pack for vRealize Orchestrator provides the ability to execute vRO workflows as part of the alerting and remediation process in vROps. The vRO workflows can be executed manually or automatically. With this solution it is easy to implement sophisticated self-healing workflows for your vROps managed environment. In this blog post I …